One of the most aspects of access control is Access cards and the card readers. If you approach your card near the reader, it would open the door and give you access to some places.
If you have been using a card, chances are that you have seen your access denied at certain doors. Especially if you have tried it on other doors that are not your organisation’s. The reason is certainly because of the programming: your card is not programmed in the database of that system. However, is it possible that your card could give you access if it has been programed ? Can all readers read all cards? And are all cards compatible with all systems ?
In this article, we will explain the operation of access cards and card readers, how they communicate, the technology they use and types of cards and readers.
card readers
We install the reader near the protected door. It reads the data from the card and send it to the panel. After comparison with its database. It Identifies whether the person carrying the card has the right to pass or not.

Types of card readers
- Proximity reader
It is the most frequently used type of readers. They are universally compatible with any access control systems, since they communicate on a Wiegand Protocol.
- Keypad reader
This kind of reader has a number pad and keyboard through which the user inputs a specific code into the system. After reading a card, it asks for a code. Then the code is verified according to the database of the system.
- Biometric reader
This reader uses the personal makeup of an individual to identify their credentials. Such as fingerprints, Iris …etc.
- Wireless readers
This kind of readers avoid wiring all doors. Hotels are the main users. They are connected via radio frequency to access points made by the same brand. Which is itself connected to the main panel for real-time update informatio
Access cards
The access control card is a card that grants access or refuses it through electronically controlled doors. It is embedded with a chip where user credentials are stocked. By approaching the card to a reader, it transmits those credentials to the system then, it determines if or not the holder has access.
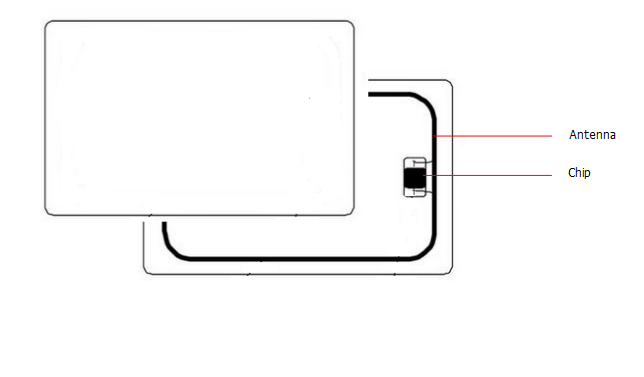
The next diagram shows the access card structure. actually, inside the plastic cover there is an antenna and a microchip
Types of access cards
- Proximity card
Proximity card is the most common card in access control. The microchip embedded within it has only one function: to provide the card’s identification number to the system, so it can be verified with a remote computer. Many access control systems only read the identification numbers and verify if it is in the database
- Smart card
It can provide identification, authentication, and store information because of the memory embedded within its microchip.
We can also program a smart card to use it as a cash card or a pre-paid membership card.
How an access card and a reader communicate ?
The way of communication between the card and the reader is a radio frequency identification (RFID)
The process of a communication is as follow:
When we approach the card to the reader, the reader induces the card. The induction is creating a current powering the integrated card’s circuit, which makes the chip emit its ID number.
Then The Reader sends the ID to panel for a verification. Then it opens the door or refuses depending the user credentials and access levels
RFID frequency range
- Low frequency RFID: it goes until 300 KHz. Proximity cards communicate generally at 125 KHz
- High frequency RFID: it reaches 30 MHz Smart cards operate 13.56 MHz
NFC communication technology
NFC stands for near-field communication. It is another of communication between reader and cards. It evolved from radio-frequency identification (RFID) technology.
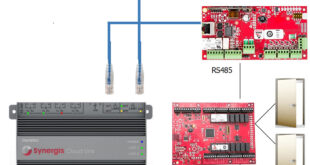
Card reader wiring diagram
The following diagram shows the standard wiring of a card reader